We’ve created a roadmap for working with companies in a way that effectively executes a solid content marketing strategy.

IT Infrastructure
IT services and solutions
IT infrastructure encompasses all the components and resources that are needed to deliver IT services and solutions within an organization. It includes both physical and virtual resources that support the storage, processing, and transmission of data. Understanding and effectively managing IT infrastructure is crucial for any organization to ensure smooth operations, enhance productivity, and maintain a competitive edge.
What’s Included?
What's Included In Our IT Infrastructure Services?
Networking
LAN (Local Area Network): Connects computers within a limited area such as a building.
WAN (Wide Area Network): Connects larger geographical areas, often multiple LANs.
Internet: Global network providing connectivity to external networks and services.
VPN (Virtual Private Network): Provides secure remote access to an organization’s network.
Data Centers
On-Premises Data Centers: Physical facilities that house servers, storage, and networking equipment.
Cloud Data Centers: Virtualized resources provided by cloud service providers (e.g., AWS, Azure, Google Cloud).
Support and Maintenance
IT Support: Helpdesk services for troubleshooting and resolving issues.
Maintenance: Regular updates, patches, and repairs to ensure systems operate efficiently.
Software
Operating Systems: Software that manages hardware resources and provides services for application software (e.g., Windows, Linux).
Database Management Systems (DBMS): Software for storing, retrieving, and managing data (e.g., SQL, Oracle).
Security Software: Antivirus, anti-malware, encryption tools, and other applications to secure the infrastructure.
Virtualization and Cloud Services
Virtual Machines (VMs): Software-based emulations of physical computers.
Containers: Lightweight, portable, and self-sufficient environments for running applications.
Cloud Computing: Delivery of computing services (servers, storage, databases, networking, software) over the internet.
Backup and Disaster Recovery
Backup Solutions: Regularly saving copies of data to prevent loss (e.g., tape backups, cloud backups).
Disaster Recovery Plans: Strategies to recover data and restore operations after a disaster.
Hardware
Servers: Machines that provide data, resources, and services to other computers in a network.
Storage Devices: Systems like hard drives, SSDs, NAS, and SAN that store data.
Network Devices: Routers, switches, firewalls, and load balancers that manage network traffic.
End-User Devices: Computers, laptops, tablets, and smartphones used by employees.
Management and Monitoring Tools
Network Monitoring: Tools to monitor network performance and identify issues (e.g., Nagios, SolarWinds).
System Management: Tools to manage and automate IT tasks (e.g., Ansible, Puppet, Chef).
Application Performance Management (APM): Tools to monitor and manage the performance of software applications.
Compliance and Governance
Compliance: Adhering to regulations and standards (e.g., GDPR, HIPAA).
Governance: Policies and procedures to manage IT resources and ensure they align with business goals.
Featured Case
We Focused on Results
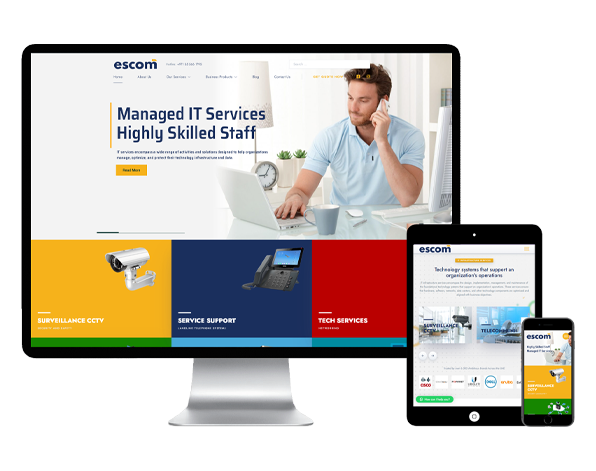
Web & Marketing
Our mission is to aid our clients in bestowing a professional front to the ma
Website Design
html, css, javascript, bootstrap, Graphic design, W3C standards
Website Development
php, wordpress, hosting
Search Engine Optimization
google, google ads, marketing

CCTV Cameras
Provide the home health care programs at flexible schedules and cost-friendly
IT Infrastructure
IT infrastructure services encompass the design, implementation, management,
Network Infrastructure
LAN, WAN, and Wi-Fi
Server Management
Physical and virtual servers
Data Center Services
Storage

Telecommunications
A Photoshop template file to help you create realistic foil balloon words
Landline Telephone Systems
Voice communication
Switching Systems
Networking Equipment

Access Control System
Provided responsive customer support and fast turnaround on a modern.
Authentication
fingerprint, iris scan, facial recognition
Reader Devices
biometric scanners
Monitoring and Logging
real-time access


 AMC / Tech Service
AMC / Tech Service IT Infrastructure
IT Infrastructure Telecommunication
Telecommunication Surveillance CCTV
Surveillance CCTV Access Control
Access Control Web & Marketing
Web & Marketing