Backing up your data is essential to protect against data loss, hardware failures, or cyberattacks. There are several de...
Data protection and data privacy are crucial for safeguarding personal and sensitive information. Here are some essentia...
Introduction to IT Infrastructure Services What is IT Infrastructure? Definition: The foundational technology environm...
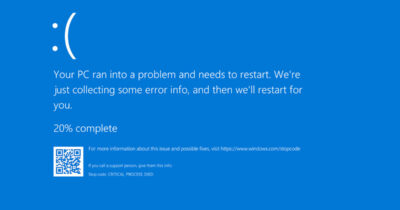
The Blue Screen of Death (BSOD) can be caused by various issues, including hardware failures, driver problems, and softw...
Network Attached Storage (NAS) devices are specialized storage systems that connect directly to a network, allowing mult...
Cloud storage offers numerous advantages, making it an increasingly popular solution for both individuals and businesses...
Microsoft 365 offers a range of advantages that make it a compelling choice for businesses and individuals. Here are som...
Biometric technology refers to the identification and verification of individuals based on their unique physical or beha...
CCTV (Closed-Circuit Television) surveillance is a crucial component of modern security systems, offering numerous benef...
1. Implement Strong Security Policies Access Control: Enforce strict access controls, ensuring that only authorized per...











 AMC / Tech Service
AMC / Tech Service IT Infrastructure
IT Infrastructure Telecommunication
Telecommunication Surveillance CCTV
Surveillance CCTV Access Control
Access Control Web & Marketing
Web & Marketing