Card Readers
Devices that read access cards to grant or deny entry.

An access control system (ACS) is a security solution that regulates who or what can view or use resources in a computing environment. It is a fundamental component of security management, helping to ensure that only authorized individuals can access certain areas or information.

Devices that read access cards to grant or deny entry.

Require a PIN for access

Use unique biological characteristics such as fingerprints, facial recognition, or iris scans.
Access control systems are vital for securing physical spaces and digital environments, ensuring that only authorized individuals can access specific areas or information. With advancements in technology, these systems are becoming more sophisticated, offering enhanced security features and greater flexibility. However, it is essential to balance security needs with privacy considerations and ensure compliance with relevant regulations. As organizations continue to evolve, access control systems will play a critical role in safeguarding assets and information.

Authentication: The process of verifying the identity of a user or device before granting access.
Authorization: Determines the level of access or permissions an authenticated user has.
Audit and Reporting: Tracks and logs access attempts, successful accesses, and denied accesses for security auditing and compliance purposes.
Time-Based Access: Restricts access based on specific times and dates, such as business hours or employee shifts.
Remote Access Management: Allows administrators to manage access control settings and monitor access remotely.
Integration with Other Systems: Integrates with surveillance cameras, alarm systems, HR databases, and other security systems for comprehensive security management.
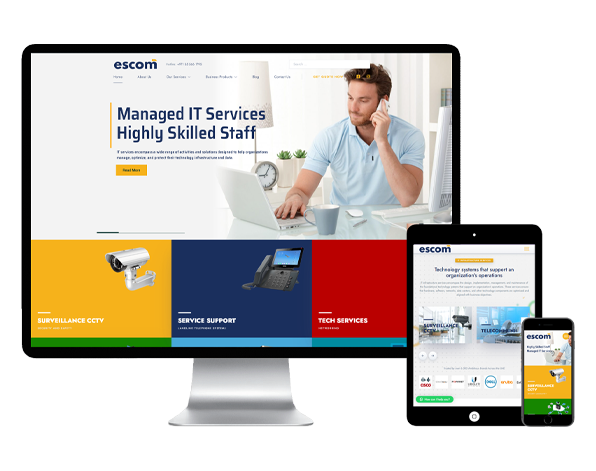
Our mission is to aid our clients in bestowing a professional front to the ma
html, css, javascript, bootstrap, Graphic design, W3C standards
php, wordpress, hosting
google, google ads, marketing

Provide the home health care programs at flexible schedules and cost-friendly
IT infrastructure services encompass the design, implementation, management,
LAN, WAN, and Wi-Fi
Physical and virtual servers
Storage

A Photoshop template file to help you create realistic foil balloon words
Voice communication

Provided responsive customer support and fast turnaround on a modern.
fingerprint, iris scan, facial recognition
biometric scanners
real-time access